A Threat Vulnerability Risk Assessment is a tool that helps businesses to identify various possible threats and risks, assess the impact and likelihood of threats, and suggest steps to be taken to mitigate the risks. It ensures proper utilization of limited resources with timely processed decisions to help mitigate disruptions. It is a critical component in holistic risk management strategy which secures organisations’ operational continuity and strengthens business resilience.
Key Definitions:
- Threat:
- An event or situation that poses a risk for the assets or operations of the organization. For example,
- Physical security threats involving robbery, civil disorder, fire outages, flooding, and natural disasters.
- Cyber threats such as data breaches, ransomware or espionage.
- Operational threats such as power outages, system failure, or disruptions in supply chains.
- Vulnerability:
- A vulnerability is a gap, lacunae, or weakness in the organisation’s infrastructure or operational process. Such a gap makes the organisation vulnerable to a specific threat increasing its risk potential.
- For example, design flaws in supply chain operations, inadequate employee training, or poor physical security measures.
- Risk:
- Risk is the probability of a negative event which includes frequency of the event and the potential impact of the disruptive event.
- Different organizations have distinct vulnerabilities and risk appetite with respect to threats.
- Risk = Threat x Vulnerability x Impact
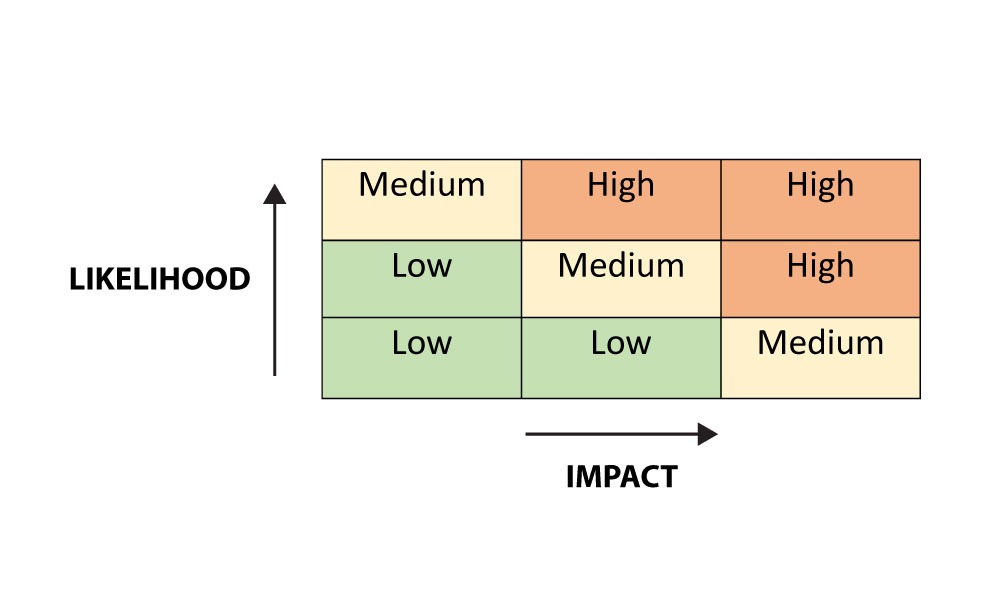
Key Components of Threat Vulnerability Risk Assessment:
- Identifying risks by an assessment of external actors and internal actors threatening the security as well as collecting data on past disruptive events.
- Conducting Vulnerability assessment to understand gaps or lacunas in the organisation’s structural process, physical and soft infrastructure as well as operation process.
- Evaluating Risks to understand the likelihood of the risk and its potential impact on the organisation.
- Prioritisation of risks with respect to specific vulnerabilities for better utilisation of resources.
- Formulating risk-mitigating strategies to reduce the impact of threats and safeguarding people, processes, and infrastructure.
- Continuous monitoring of the risk management strategy by identifying any gaps or room for improvement.
Leveraging Technology and tools for better Threat Risk Assessment Models
To identify, assess, and mitigate threats, state-of-the-art technologies such as big data analytics, AI-machine learning, and geospatial analysis tools can be used.
- AI and machine learning can scan data and monitor developments for early warning of forthcoming risks and vulnerabilities.
- Automation tools can assist in the supervision of repetitive tasks such as scanning, reporting, and management.
- Cloud services centralize data management on a centralized dashboard allowing real-time monitoring.
Challenges in Adopting Threat Vulnerability Risk Assessment
- Complex and interconnected security landscape and evolving threats increase the volume of new vulnerabilities and risks. This makes it difficult for organisations to identify patterns and risks.
Integration of technological tools such as AI and cloud-based services along with subject matter experts can help in managing evolving risks and vulnerabilities.
- Poor prioritisation of risks based on vulnerabilities often leads to an under-optimal utilization of resources and monetary losses.
Performing vulnerability assessment according to organisation’s risk appetite helps prioritise risks. Effective collaboration with a risk consultancy firm and subject matter experts can help in better prioritisation.
- Lack of awareness amongst employees or key stakeholders may make the organisation vulnerable to new threats. Human factors such as negligence and resistance to change can posit new challenges to security framework.
Regular training and awareness programs can help employees to face new security challenges.
Organisations can identify and assess the likelihood of possible threats and give particular emphasis to risks while ascertaining risk levels according to the vulnerabilities with the help of Threat Vulnerability Risk Assessment. This would help improve security resilience within the infrastructure, structural protocols, and processes of the organisation.
Partner with MitKat to build a robust Threat Vulnerability Risk Assessment
Mitkat helps organisations to navigate through an uncertain evolving security landscape and disruptive events that hamper business continuity. We ensure that our tailor-made risk assessments and risk-mitigating strategies help increase the security resilience of organisations. Our AI-powered operational risk monitoring tool, datasurfr combined with experts enables companies to stay abreast of evolving operational risks and emerging developments.






